Today we are surrounded by an ever-increasing array of connected devices. Electronic payments are becoming more popular, and we are keeping more and more personal information in the cloud. At the same time, risks continue to rise as hackers get better and better at breaking down security schemes.
Regardless of the end application, security must be based on a multi-layered approach starting with the deepest embedded hardware. This starts within the manufacturing process of the chips themselves and includes a broad range of hardware primitives serving as security keys such as True Random Number Generator (TRNG) and physical unclonable functions (PUFs).
Security founded on manufacturing variations
A PUF is a technique that leverages the inherent physical variations in manufacturing processes to generate unique and unpredictable responses for each individual chip. Each instance of a hardware device exhibits slight variations in its electrical characteristics due to manufacturing variations, such as transistor size, doping levels, and other process parameters, and these variations can create a unique ‘fingerprint’ for each device. This hardware-based mechanism can be used to establish trust and ensure the uniqueness of each device without the need for stored secrets or traditional cryptographic algorithms.
PUFs are getting increasing attention as a hardware approach for information security in IoT devices. Since IoT devices have constrained area and power requirements and are often deployed in harsh environments, it is critical that the PUF be cost-efficient in terms of area per bit, and reliable with low bit error rate (BER).
PUFs can be based on a range of characteristics implemented on CMOS technology. Examples of strong PUFs are those based on ring oscillators while weaker PUFs are based on SRAM, Butterfly, and Flip-flops. Since these are all implemented on CMOS, they require large area, and also face difficulties in scaling beyond 10nm. Such conventional PUF schemes generally suffer from poor area efficiency and high BER under process, voltage and temperature (PVT) variations. While stabilization and error correction techniques can help to improve the output reliability, they result in considerable costs in area and power.
ReRAM – an inherently secure technology
ReRAM (or RRAM) has been investigated to implement efficient PUFs by using inherent variations in storage resistance, switching time and nonlinearity.
In addition, ReRAM has inherent physical attributes that enable it to protect its content from hacking attacks and make it more difficult to reverse engineer. Since ReRAM does not use any charges or other particles like flash does, it is more difficult to sense or change its internal state using electron beams. ReRAM can also easily withstand magnetic attacks because it is immune to electromagnetic fields. Because the ReRAM bit cell is deeply embedded between two metal layers integrated at the back-end-of-line (BEOL), it is also more immune to optical (laser) attacks. In addition, careful design of Weebit ReRAM cells and their associated control logic enables a balanced power profile which makes it less vulnerable to power analysis hacking.
Above: The ReRAM bit cell is deeply embedded between two
metal layers integrated at the back-end-of-line (BEOL)
Given all of this, ReRAM is an ideal solution for PUFs and other security mechanisms. In addition, ReRAM requires less area than traditional PUF schemes because it is integrated in BEOL.
At the recent International Memory Workshop, I presented a poster session based on a new paper written by technologists from the Indian Institute of Technology Delhi, led by Prof Manan Suri and Vivek Parmar, CEA-Leti and Weebit. The paper presents a ReRAM PUF with excellent reliability, demonstrating immunity to modern ML-based SCA (side-channel-attacks) by introducing a secondary low-energy HRS (high-resistance state) programming step.
The paper highlights the benefits of using Weebit ReRAM to provide PUF capability. In it, we successfully demonstrate and validate the design of a 2T-2R based PUF over a large array of 16Kb developed using Weebit’s technology by exploiting Vform variability between devices in consecutive rows. The design is validated for two different ReRAM stacks at 130nm and using one stack at 28nm.
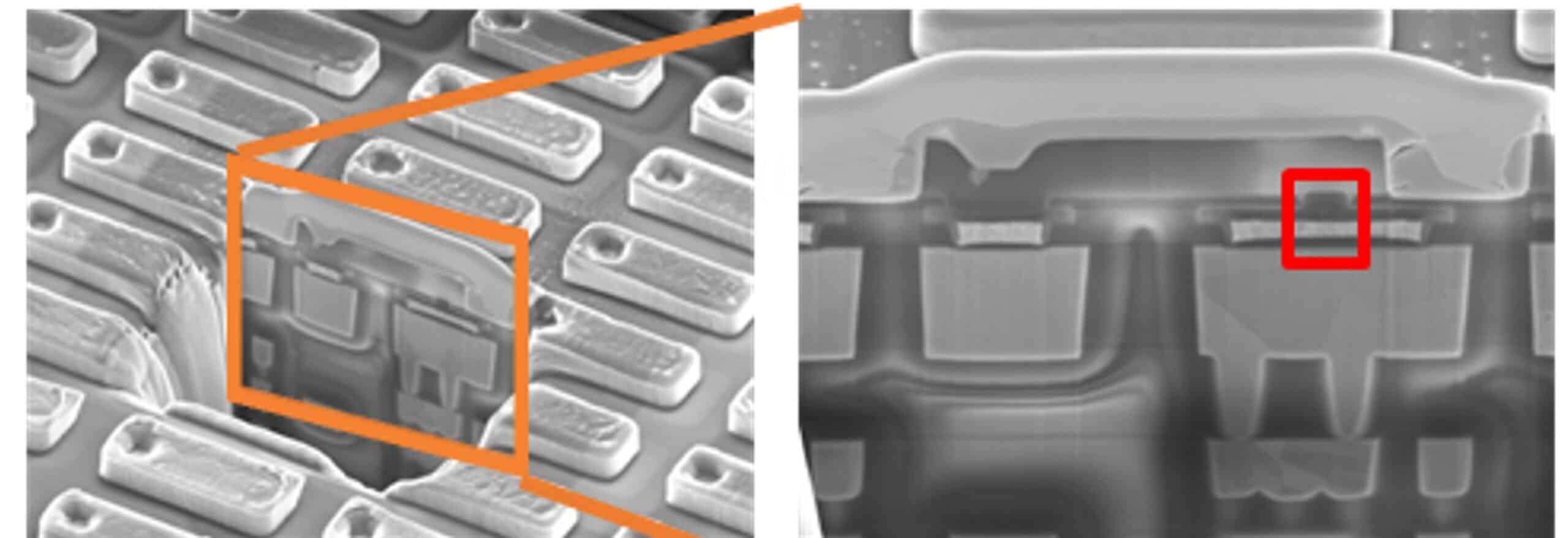
Above: TEM (transmission electron microscope) image of fabricated ReRAM array at 130nm: a) top view; b) cross section with ReRAM device highlighted
The arrays show high immunity to the high-temperature SMT (surface mount technology)-reflow process that is critical to electronic component manufacturing. The ReRAM PUF arrays also demonstrate resilience against modern Machine-Learning (ML) based side channel attacks (SCAs), a growing security threat for chips today. In addition, the fabricated arrays exhibit excellent performance in terms of speed, data retention and memory window.
You can read the paper here.